Recording Encryption
Updated
Sprinklr provides encryption for in-house recordings in accordance with industry standards to ensure compliance. The following is a simplified architectural workflow outlining the process:
Store Encrypted Recordings
Follow these steps to store encrypted recordings:
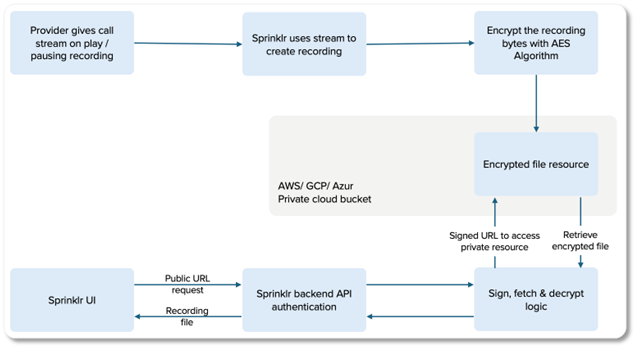
Unique encryption setup: Each Sprinklr environment is assigned its own encryption key to maintain data security across different environments.
Data encryption: When a call is recorded, the raw recording data is encrypted using a combination of a unique encryption key and a randomly generated Initialization Vector (IV). This encryption follows the industry-standard AES-GCM 256-bit cipher, ensuring the highest level of security.
Secure storage: The encrypted recording data is then saved into a file, which is securely uploaded to a private cloud storage bucket hosted on AWS, GCP, or Azure.
Private URL creation: A private URL is generated for the stored encrypted file and saved within Sprinklr’s internal system. This URL is protected and never publicly exposed. If accessed, it requires Sprinklr’s authorization signature, preventing unauthorized access.
Public URL with reverse proxy: A public URL is also created, which points to Sprinklr’s backend system. This URL acts as a reverse proxy, meaning external users don’t interact directly with the private storage. Instead, the public URL directs requests to the secure backend, which manages access and security.
Access Encrypted Recordings
Follow these steps to access encrypted recordings:
Accessing the recording: Users retrieve the public URL through the Care Console or Quality Management (QM) View.
Request for playback: The user interface (UI) sends a request to the public URL to access the recording.
Authentication: The request is sent to the Sprinklr backend, where the system checks that the request comes from an authenticated and authorized user logged into the correct Sprinklr environment.
Fetching the private URL: Upon successful authentication, the backend retrieves the corresponding private URL for the encrypted recording file.
Secure retrieval: The backend signs the private URL, authorizing it, and then fetches the encrypted recording file from the cloud storage.
Decryption: The recording file is decrypted by using the stored encryption key and the corresponding Initialization Vector (IV).
Playback or download: The decrypted recording is sent back to the UI, where it is either played or made available for download by the user.