Transform CX with AI at the core of every interaction
Unify fragmented interactions across 30+ voice, social and digital channels with an AI-native customer experience platform. Deliver consistent, extraordinary brand experiences at scale.
Contact Center Security in 2025: Common Threats and Fixes
Your contact center holds a wealth of sensitive customer information — from purchase histories and phone numbers to, in some cases, social security numbers.
Now, picture this: a cybercriminal, smarter than you anticipated, breaches your contact center security and steals that data. The fallout?
An upset customer takes to X (formerly Twitter) to share their experience and your brand faces the brunt of the reputational damage. While this could be a real-world test of your social media and PR teams’ crisis management skills, it’s a situation no business wants to be in. According to Statista, the average data breach cost in the United States reached $9.48 million in 2023, up from $9.44 million the previous year.
Given the large amounts of customer data they manage, contact centers are frequent targets for cybercriminals, making strong contact center security a necessity. From identity fraud to voice manipulation, to phishing attacks, the risks are too high to ignore.
That’s why ensuring robust contact center security and following best practices to protect sensitive data has never been more critical.
What is contact center security?
Contact center security safeguards the data and communications that flow through your contact center. It encompasses a comprehensive set of protocols, measures and technologies designed to protect customer information from unauthorized access, data breaches and cyber threats.
3 common security threats to watch out for in your contact center
Maintaining the security of your contact center requires an understanding of the cybersecurity threats that could target your organization. Let’s explore some of the most pressing threats, their impact and how to counter them:
1. Social engineering attacks
Data breaches can occur through various attack vectors, making them a significant concern for contact centers. Social engineering attacks prey on human psychology and behavior, making them uniquely dangerous. These tactics manipulate individuals into revealing sensitive information like financial details or login credentials. One prevalent social engineering method is phishing, where cybercriminals use deceptive emails or messages that appear to be from trusted sources to trick employees into revealing sensitive information or clicking on malicious links. In a business email compromise (BEC) attack, a hacker might pose as a company executive to gain unauthorized access. This can lead to unauthorized access to your customer data. Approximately 3.4 billion malicious emails are sent daily, establishing social engineering as a primary driver of cyberattacks.
Such an event can lead to a significant loss of customer trust, as clients may begin to doubt the security of their data with your business. Beyond reputational damage, the financial and legal consequences can also include fines, legal action, and the cost of remediation.
2. Voice deepfake scams
In the past, creating convincing deepfake audio required extensive voice recordings. But with generative AI, the process has become alarmingly quick and easy. Cybercriminals are leveraging this technology to create deceptively realistic audio, tricking users and contact center agents into revealing sensitive information. This deceptive nature of deepfake technology calls for heightened vigilance and verification in communication.
For instance, an employee in a multi-national company in Hong Kong recently received a call he believed was from his company's CFO, instructing him to transfer $25.6 million. Only after the transfer did he realize a deepfake heist had deceived him.
🔧 How to tackle deepfake challenges
Start by training your employees. A well-informed team is your first defense against threats like deepfake technology. Educating them on the latest tactics and providing a solid knowledge base comprising practical tips and tools can prevent many attacks. Regularly training employees to recognize phishing attempts and deepfake scams during calls ensures they can spot and report suspicious activity directly. Learn more: What is Knowledge Base & How to Build it in 2024
3. Insider threats
Insider threats involve malicious actions or negligence by employees, contractors or other internal personnel who access the organization's systems and data. These can range from intentional data theft to accidental data exposure. Insider threats are particularly dangerous because they come from trusted individuals with legitimate access to sensitive information.
Contact center security best practices
Keeping your contact center data secure is more important than ever. Here is a step-by-step guide:
Assess security infrastructure
The first step to fortifying your contact center is assessing your existing contact center technology. Start by identifying the assets, resources and data that need protection. These could include customer information, transaction records and communication logs.
Assign access control
One of the most effective ways to secure sensitive information is through role-based access control. This method limits access to data and resources based on your employee’s role. For instance, customer service representatives may access customer information, not financial records or internal communications. This reduces the risk of unauthorized entry and potential data breaches.
💡 Pro Tip: Leverage your contact center software to limit who can access sensitive information. Utilize filters based on roles, user groups and properties to strengthen security. Also, empower customers with self-service options. Let customers handle their needs independently instead of sharing sensitive information on direct channels.
Encrypt your data
Encryption is a powerful tool for protecting your data from cyberattacks. When encrypted, data is converted into a code that can only be deciphered by someone with the correct encryption key. There are two types of encryption: encryption at rest and encryption in transit. Encryption at rest protects data stored on your servers or databases. In contrast, encryption in transit protects data as it moves across networks, such as during email communication or file transfers.
🤺 How Sprinklr combats data breaches
Sprinklr prioritizes protecting customer data and staying one step ahead of potential threats. For example, Sprinklr’s live chat support software is designed with robust security features that add multiple layers of protection, ensuring your customer interactions remain secure and confidential. Here’s how:
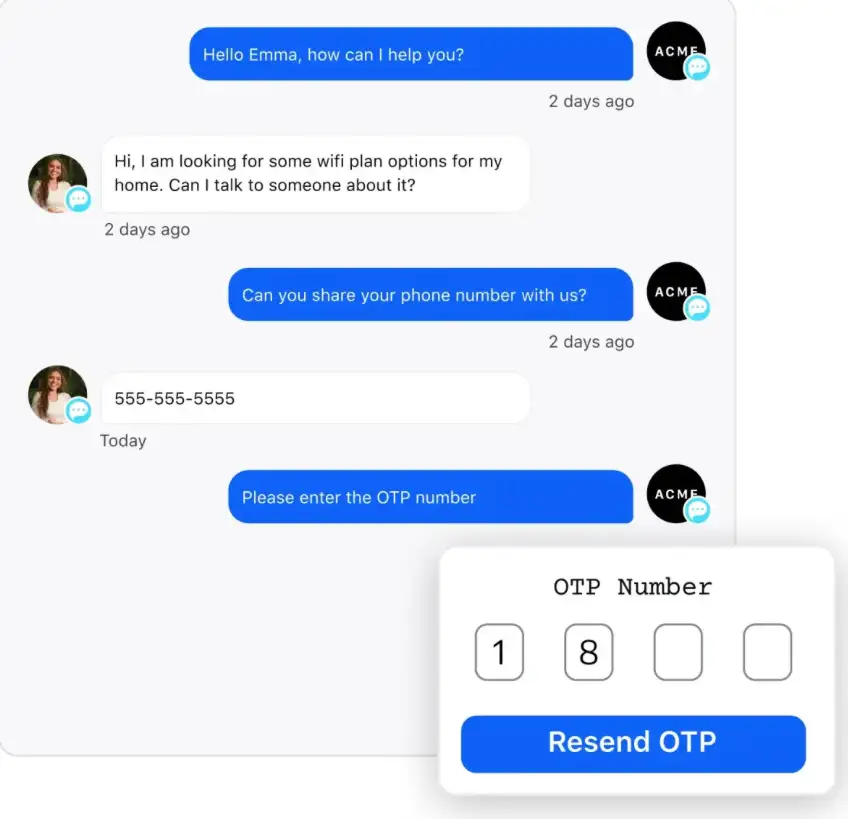
Single sign-on (SSO): You can streamline and secure user authentication by allowing customers to access multiple services with a single set of login credentials. This reduces the risk of password fatigue and minimizes the potential for unauthorized access.
OTP validations: One-time password (OTP) validations enhance security, ensuring that only verified users can access sensitive information during chat sessions.
Secure chat links: Generate secure chat links that encrypt conversations end-to-end, protecting the data as it travels between the user’s device and your contact center.
Secure handshakes: Implement secure handshakes between your website, app and chat interface, ensuring that data is transmitted safely and only to intended recipients.
Implement continuous monitoring
Continuous monitoring is essential for maintaining a high level of security in your contact center. Automated monitoring systems can constantly monitor your network, identifying and alerting you to potential threats in real time. These systems are designed to detect unusual activities, such as a sudden spike in login attempts, unfamiliar bots or anomalies in data usage patterns.
Contact Center Security Trends to Watch in 2025
Several key trends are emerging in 2025 that will shape the landscape of contact center security. Understanding and integrating these trends will be crucial for businesses to avoid potential threats and safeguard sensitive customer data.
1. AI-based threat detection
With AI-based threat detection, your contact center can identify real-time risks and initiate action. The technology doesn’t just react to threats—it predicts them by analyzing patterns and identifying anomalies. The systems use machine learning algorithms to detect unusual patterns in network traffic, user behavior and system logs, flagging potential security breaches before they cause harm.
2. Zero trust architecture
The traditional approach of trusting everything within a network perimeter is rapidly becoming obsolete. In 2025, Zero Trust Architecture (ZTA) is set to become a standard security framework for contact centers. ZTA operates on the principle of "never trust, always verify," ensuring that every user, device and connection is authenticated and authorized before access is granted. This trend is driven by the increasing complexity of hybrid work environments, where employees may access contact center systems from various locations and devices.
3. Enhanced data encryption practices
With the growing prevalence of data breaches, encryption remains a critical component of contact center security. In 2025, advanced encryption methods, such as homomorphic encryption and quantum-resistant algorithms, are expected to be more widely adopted. These methods offer stronger protection for data both at rest and in transit, making it significantly more difficult for attackers to intercept or decipher sensitive information.
4. Integration of cybersecurity with customer experience
Security and customer experience are no longer separate domains. In 2025, a greater focus is on integrating cybersecurity measures seamlessly with customer interactions. This includes ensuring that security protocols do not disrupt the but instead enhance it, such as using secure, encrypted customer communication channels or implementing customer-friendly authentication processes that balance security with convenience.
Protecting your contact centers from emerging threats
For many enterprises, keeping up with ever-changing security threats while staying focused on core contact center business objectives is daunting. The pressure to safeguard sensitive customer data can be overwhelming, often stretching your team thin and leaving your business vulnerable to potential breaches.
This is where Sprinklr Service steps in. With comprehensive insights and unified platform built to stay ahead of evolving threats. The exhaustive security measures, from state-of-the-art encryption to proactive threat monitoring, are designed to handle the complexities of today’s cybersecurity challenges.
Built on the Unified-CXM platform, trusting Sprinklr means you can refocus on what truly matters—delivering exceptional customer experiences and driving your business forward.








